A cybersecurity scan of hundreds of media industry vendors showed that many companies are slow to fix critical vulnerabilities, according to MDR and third-party risk management provider BlueVoyant.
The media industry faces various types of cybersecurity incidents, including content leaks to torrent sites and dark web forums, disruptions to channels used to deliver content to consumers, and other disruptive attacks, such as as ransomware and denial of service (DoS).
BlueVoyant analyzed nearly 500 suppliers. This includes 49 companies that provide content management, production, monetization and distribution services to most media companies, and 436 companies that represent vendors whose products and services are widely used but not common to the whole sector.
Of all those companies, 143 had what the security firm calls “zero tolerance findings,” which are critical vulnerabilities in internet-connected systems that are commonly targeted by threat actors.
One or more of these vulnerabilities have been identified in approximately 30% of media providers, which BlueVoyant says is nearly double the cross-industry average seen in over 1 million companies.
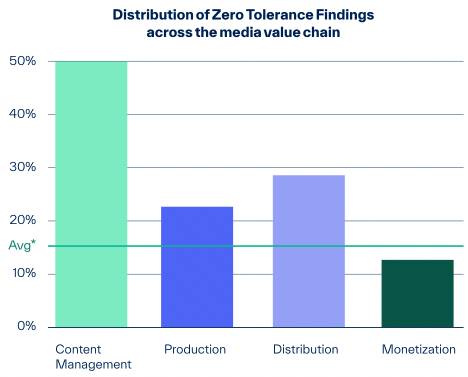
Looking at the distribution of these vulnerabilities, content management vendors appear to be the most affected, with half of these vendors hosting vulnerable systems. The monetization segment is best at securing systems, with less than 15% exposing their systems to attacks.
As a specific example, BlueVoyant provided the Confluence vulnerability identified as CVE-2022-26134. Atlassian released a patch in early June, but the malicious exploit started at least a week before.
Although this is a severe vulnerability that can be remotely exploited to take full control of the targeted system and cause serious harm to affected organizations, BlueVoyant found that eight of the monitored media industry vendors n still hadn’t applied the patch six weeks after it was released.
“Media companies need to take strong action with their vendors and suppliers, especially when it comes to content management. Supply chain attacks are a common attack vector, and protecting against ecosystem vulnerabilities is key to preventing leaks, downtime, and interruptions to the production process,” said BlueVoyant. in his report (direct pdf download).
Earlier this summer, the cybersecurity firm analyzed 300 SMB contractors for the defense industrial base sector and found that many were vulnerable to attack and some had likely already been compromised.
Related: Over 28,000 vulnerabilities disclosed in 2021
Related: Ransomware-Related Data Leaks Nearly Doubled in 2021